Service Discovery Using Communication Fingerprints
Olivia Oanea, Jan Sürmeli and Karsten Wolf. Service Discovery Using Communication Fingerprints Submitted.
Authors
Olivia Oanea (Universität Rostock, 18051 Rostock, German)
Jan Sürmeli (Humboldt-Universität zu Berlin, Unter den Linden 6, 10099 Berlin, Germany)
Karsten Wolf (Universität Rostock, 18051 Rostock, Germany)
Case Study
Tools
You can download the tools which we used in our case study.
For each tool, do the following
Download the most recent version of Linda/Yasmina/LoLA at http://service-technology.org/files/linda, http://service-technology.org/files/yasmina and http://service-technology.org/files/lola
- Unpack them by executing
tar xfz lola-x.tar.gz
- Configure them by executing
cd lola-x
./configure
where lola may be replaced by the respective tool
Process Models
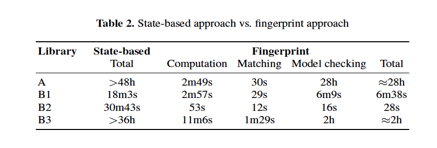
Experiments were performed on both services and their partners obtained from decomposing process models from 4 libraries (A, B1, B2, B3).
* For fingerprint/fingerprint compatibility check download the services and their partners in OWFN file format: A,B1,B2,B3
* For state space analysis, download the compositions in LoLA file format and the task files, A lola files, B1 lola files, B2 lola files, B3 lola files
Obtain Fingerprints with Linda
To compute octagon (using terms of type x-y, x+y, x) fingerprints for open nets, execute
linda net.owfn -2 -o net.output
Check Compatibility with Yasmina
To execute compatibility check using ILP using the fingerprint/fingerprint check
yasmina -m net.output -m netpartner.output
Check Compatibility with LoLA
To use LoLA to check for weak termination of composed processes, proceed as follows:
- Compile another version of LoLA to check for liveness of state predicate by executing
make lola-liveprop1
- Execute
lola-liveprop1 net.lola -a netpartner.task
Results
The experimental results comparing the state-based approach vs. the fingerprint approach are depicted in the following table.